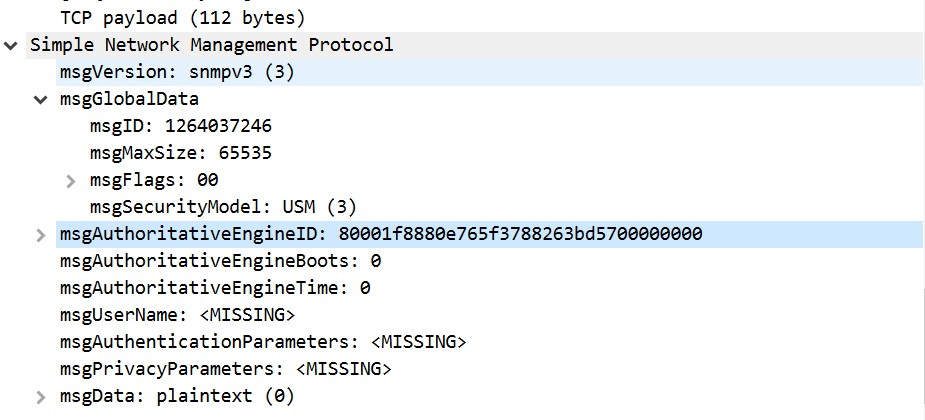
I have added the MPv3 model to snmp and now i am seeing not in time window error in output and because of this i dont see the processPdu method getting invoked. Please suggest i have added the auto discovery for the USM .
Code:
package snmpsimple;
import java.io.IOException;
import org.snmp4j.CommandResponder;
import org.snmp4j.CommandResponderEvent;
import org.snmp4j.MessageDispatcherImpl;
import org.snmp4j.Snmp;
import org.snmp4j.TransportMapping;
import org.snmp4j.log.ConsoleLogAdapter;
import org.snmp4j.log.ConsoleLogFactory;
import org.snmp4j.log.LogFactory;
import org.snmp4j.mp.MPv3;
import org.snmp4j.security.AuthMD5;
import org.snmp4j.security.AuthSHA;
import org.snmp4j.security.AuthenticationProtocol;
import org.snmp4j.security.PrivAES128;
import org.snmp4j.security.PrivDES;
import org.snmp4j.security.PrivacyProtocol;
import org.snmp4j.security.SecurityProtocols;
import org.snmp4j.security.USM;
import org.snmp4j.security.UsmUser;
import org.snmp4j.smi.Address;
import org.snmp4j.smi.GenericAddress;
import org.snmp4j.smi.OctetString;
import org.snmp4j.smi.TcpAddress;
import org.snmp4j.smi.UdpAddress;
import org.snmp4j.transport.DefaultTcpTransportMapping;
import org.snmp4j.transport.DefaultUdpTransportMapping;
import org.snmp4j.util.MultiThreadedMessageDispatcher;
import org.snmp4j.util.ThreadPool;
public class SnmpTrapReceiver {
static {
LogFactory.setLogFactory(new ConsoleLogFactory());
ConsoleLogAdapter.setDebugEnabled(true);
}
private static final String SNMP_PORT = System.getenv("SNMP_PORT");
private static final String SNMP_AUTH_PROTOCOL = System.getenv("SNMP_AUTH_PROTOCOL");
private static final String SNMP_PRIVACY_PROTOCOL = System.getenv("SNMP_PRIVACY_PROTOCOL");
private static final String SNMP_AUTH_PHRASE = System.getenv("SNMP_AUTH_PHRASE");
private static final String SNMP_PRIVACY_PHRASE = System.getenv("SNMP_PRIVACY_PHRASE");
private static final String SNMP_PROTOCOL = System.getenv("SNMP_PROTOCOL");
private static final String SNMP_USER=System.getenv("SNMP_USER");
private static final String NOTIFICATION_PORT = System.getProperty("NOTIFICATION_PORT","1163");
public static void main(String[] args) {
try {
System.out.println(SNMP_PORT);
System.out.println(SNMP_AUTH_PROTOCOL);
System.out.println(SNMP_USER);
//MPv3.createLocalEngineID()
Address listenAddress, notificationAddress;
ThreadPool threadPool = ThreadPool.create("Trap", 2);
MultiThreadedMessageDispatcher dispatcher =
new MultiThreadedMessageDispatcher(threadPool,
new MessageDispatcherImpl());
// Create transport mapping
TransportMapping<?> transport;
if ("TCP".equalsIgnoreCase(SNMP_PROTOCOL)) {
listenAddress = GenericAddress.parse("tcp:0.0.0.0/"+SNMP_PORT);
notificationAddress = GenericAddress.parse("tcp:0.0.0.0/"+NOTIFICATION_PORT);
transport = new DefaultTcpTransportMapping((TcpAddress)listenAddress);
} else {
listenAddress = GenericAddress.parse("udp:0.0.0.0/"+SNMP_PORT);
transport = new DefaultUdpTransportMapping((UdpAddress)listenAddress);
notificationAddress = GenericAddress.parse("udp:0.0.0.0/"+NOTIFICATION_PORT);
}
transport.listen();
SecurityProtocols securityProtocols = SecurityProtocols.getInstance();
AuthenticationProtocol authProtocol = getAuthProtocol(SNMP_AUTH_PROTOCOL);
PrivacyProtocol privProtocol = getPrivProtocol(SNMP_PRIVACY_PROTOCOL);
if (authProtocol != null) {
securityProtocols.addAuthenticationProtocol(authProtocol);
}
if (privProtocol != null) {
securityProtocols.addPrivacyProtocol(privProtocol);
}
byte[]engineID = MPv3.createLocalEngineID();
// Create user
OctetString authKey = new OctetString(SNMP_AUTH_PHRASE);
OctetString privKey = new OctetString(SNMP_PRIVACY_PHRASE);
UsmUser user = new UsmUser (new OctetString(SNMP_USER),
authProtocol.getID(),
authKey,
privProtocol.getID(),
privKey);
System.out.println("Local engineid:"+OctetString.fromByteArray(engineID).toHexString());
USM usm = new USM(securityProtocols,
new OctetString(engineID), 0);
usm.setEngineDiscoveryEnabled(true);
usm.addUser(user);
//SecurityModels.getInstance().addSecurityModel(usm);
//snmp.setLocalEngine(engineID, 0, 0);
MPv3 mpv3= new MPv3(usm);
//mpv3.getSecurityModels().addSecurityModel(usm);
dispatcher.addMessageProcessingModel(mpv3);
// Create SNMP object
Snmp snmp = new Snmp(dispatcher,transport);
//snmp.addCommandResponder(new TrapListener());
snmp.addNotificationListener(notificationAddress, new TrapListener());
snmp.discoverAuthoritativeEngineID(listenAddress, 5000);
// Set up security protocols
System.out.println("Listening for SNMP traps on port " + SNMP_PORT + " using " + SNMP_PROTOCOL);
// Keep the application running
while (true) {
Thread.sleep(1000);
}
} catch (IOException | InterruptedException e) {
e.printStackTrace();
}
}
private static AuthenticationProtocol getAuthProtocol(String protocol) {
switch (protocol.toUpperCase()) {
case "SHA":
return new AuthSHA();
case "MD5":
return new AuthMD5();
default:
System.err.println("Unsupported authentication protocol: " + protocol);
return null;
}
}
private static PrivacyProtocol getPrivProtocol(String protocol) {
switch (protocol.toUpperCase()) {
case "AES":
return new PrivAES128();
case "DES":
return new PrivDES();
default:
System.err.println("Unsupported privacy protocol: " + protocol);
return null;
}
}
static class TrapListener implements CommandResponder {
@Override
public void processPdu(CommandResponderEvent arg0) {
System.out.println("Received SNMP Trap:" +arg0.getPDU());
}
}
}
Output:
$ java -cp “snmp4j-2.8.18.jar:.” snmpsimple.SnmpTrapReceiver
1168
SHA
notlsuser
2025-05-24 16:27:16.710 main INFO TCP address 0.0.0.0/1168 bound successfully
2025-05-24 16:27:16.724 main DEBUG Initialized Salt to 76f63054f8d731d5.
Local engineid:80:00:13:70:01:7f:00:01:01:bd:df:0c:88
2025-05-24 16:27:16.733 main DEBUG Adding user notlsuser = UsmUser[secName=notlsuser,authProtocol=1.3.6.1.6.3.10.1.1.3,authPassphrase=authPass,privProtocol=1.3.6.1.6.3.10.1.2.2,privPassphrase=privPass,localizationEngineID=null]
2025-05-24 16:27:16.739 main INFO TCP address 0.0.0.0/1163 bound successfully
2025-05-24 16:27:16.739 main INFO Added notification listener for address: 0.0.0.0/1163
2025-05-24 16:27:16.743 main DEBUG RFC3414 §3.1.4.b Outgoing message is not encrypted
2025-05-24 16:27:16.743 main DEBUG Adding cache entry: StateReference[msgID=45166,pduHandle=PduHandle[1796148982],securityEngineID=,securityModel=org.snmp4j.security.USM@108c4c35,securityName=,securityLevel=1,contextEngineID=,contextName=,retryMsgIDs=null]
2025-05-24 16:27:16.744 main DEBUG Running pending sync request with handle PduHandle[1796148982] and retry count left 0
2025-05-24 16:27:16.744 main DEBUG Looking up connection for destination ‘0.0.0.0/1168’ returned: null
2025-05-24 16:27:16.744 main DEBUG {}
2025-05-24 16:27:16.744 main DEBUG Socket for address ‘0.0.0.0/1168’ is closed, opening it…
2025-05-24 16:27:16.745 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is acceptable
2025-05-24 16:27:16.745 main DEBUG Trying to connect to 0.0.0.0/1168
2025-05-24 16:27:16.747 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Adding operation 1 for: SocketEntry[peerAddress=127.0.0.1/42174,socket=Socket[addr=/127.0.0.1,port=42174,localport=1168],lastUse=Mon Jan 05 15:58:29 UTC 1970,readBufferPosition=-1,socketTimeout=null]
2025-05-24 16:27:16.748 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Firing transport state event: org.snmp4j.transport.TransportStateEvent[source=org.snmp4j.transport.DefaultTcpTransportMapping@7bf6b6c1,peerAddress=127.0.0.1/42174,newState=1,cancelled=false,causingException=null]
2025-05-24 16:27:16.748 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is reading
2025-05-24 16:27:16.748 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Reading header 0 bytes from 127.0.0.1/42174
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG No socket entry found for incoming address 127.0.0.1/42174 for incomplete message with length 0
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Adding operation 8 for: SocketEntry[peerAddress=0.0.0.0/1168,socket=Socket[unconnected],lastUse=Mon Jan 05 15:58:29 UTC 1970,readBufferPosition=-1,socketTimeout=null]
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is connectable
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Connected to 0.0.0.0/1168
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Adding operation 4 for: SocketEntry[peerAddress=0.0.0.0/1168,socket=Socket[addr=/0.0.0.0,port=1168,localport=42174],lastUse=Mon Jan 05 15:58:29 UTC 1970,readBufferPosition=-1,socketTimeout=org.snmp4j.transport.DefaultTcpTransportMapping$SocketTimeout@3ac39c1a]
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Fire connected event for 0.0.0.0/1168
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Firing transport state event: org.snmp4j.transport.TransportStateEvent[source=org.snmp4j.transport.DefaultTcpTransportMapping@7bf6b6c1,peerAddress=0.0.0.0/1168,newState=1,cancelled=false,causingException=null]
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is writable
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Sent message with length 60 to 0.0.0.0/1168: 30:3a:02:01:03:30:10:02:03:00:b0:6e:02:03:00:ff:ff:04:01:04:02:01:03:04:10:30:0e:04:00:02:01:00:02:01:00:04:00:04:00:04:00:30:11:04:00:04:00:a0:0b:02:01:00:02:01:00:02:01:00:30:00
2025-05-24 16:27:16.749 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Adding operation 1 for: SocketEntry[peerAddress=0.0.0.0/1168,socket=Socket[addr=/0.0.0.0,port=1168,localport=42174],lastUse=Mon Jan 05 15:58:29 UTC 1970,readBufferPosition=-1,socketTimeout=org.snmp4j.transport.DefaultTcpTransportMapping$SocketTimeout@3ac39c1a]
2025-05-24 16:27:16.750 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is writable
2025-05-24 16:27:16.750 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is readable
2025-05-24 16:27:16.750 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is reading
2025-05-24 16:27:16.750 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Reading header 6 bytes from 127.0.0.1/42174
2025-05-24 16:27:16.750 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Message length is org.snmp4j.transport.MessageLength[headerLength=2,payloadLength=58]
2025-05-24 16:27:16.750 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Message completed with 60 bytes and 60 buffer limit
2025-05-24 16:27:16.750 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Received message from 127.0.0.1/42174 with length 60: 30:3a:02:01:03:30:10:02:03:00:b0:6e:02:03:00:ff:ff:04:01:04:02:01:03:04:10:30:0e:04:00:02:01:00:02:01:00:04:00:04:00:04:00:30:11:04:00:04:00:a0:0b:02:01:00:02:01:00:02:01:00:30:00
2025-05-24 16:27:16.751 Trap.0 DEBUG SNMPv3 header decoded: msgId=45166, msgMaxSize=65535, msgFlags=04, secModel=3
2025-05-24 16:27:16.752 Trap.0 DEBUG RFC3414 §3.2.3 Unknown engine ID:
2025-05-24 16:27:16.752 Trap.0 DEBUG Adding cache entry: StateReference[msgID=45166,pduHandle=PduHandle[1796148983],securityEngineID=,securityModel=org.snmp4j.security.USM@108c4c35,securityName=,securityLevel=1,contextEngineID=,contextName=,retryMsgIDs=null]
2025-05-24 16:27:16.752 Trap.0 DEBUG Removed msgId retry cache sub-entry: 45166 from msgIdToPduHandleMapping: PduHandle[1796148983]
2025-05-24 16:27:16.752 Trap.0 DEBUG Removed cache entry: StateReference[msgID=45166,pduHandle=null,securityEngineID=,securityModel=org.snmp4j.security.USM@108c4c35,securityName=,securityLevel=1,contextEngineID=,contextName=,retryMsgIDs=null] for PduHandle PduHandle[1796148983]
2025-05-24 16:27:16.753 Trap.0 DEBUG Popped cache entry: StateReference[msgID=45166,pduHandle=PduHandle[1796148983],securityEngineID=,securityModel=org.snmp4j.security.USM@108c4c35,securityName=,securityLevel=1,contextEngineID=,contextName=,retryMsgIDs=null] for msgID 45166
2025-05-24 16:27:16.753 Trap.0 DEBUG RFC3414 §3.1.4.b Outgoing message is not encrypted
2025-05-24 16:27:16.753 Trap.0 DEBUG Looking up connection for destination ‘127.0.0.1/42174’ returned: SocketEntry[peerAddress=127.0.0.1/42174,socket=Socket[addr=/127.0.0.1,port=42174,localport=1168],lastUse=Mon Jan 05 15:58:29 UTC 1970,readBufferPosition=-1,socketTimeout=org.snmp4j.transport.DefaultTcpTransportMapping$SocketTimeout@77b7a02b]
2025-05-24 16:27:16.753 Trap.0 DEBUG {0.0.0.0/1168=SocketEntry[peerAddress=0.0.0.0/1168,socket=Socket[addr=/0.0.0.0,port=1168,localport=42174],lastUse=Mon Jan 05 15:58:29 UTC 1970,readBufferPosition=-1,socketTimeout=org.snmp4j.transport.DefaultTcpTransportMapping$SocketTimeout@3ac39c1a], 127.0.0.1/42174=SocketEntry[peerAddress=127.0.0.1/42174,socket=Socket[addr=/127.0.0.1,port=42174,localport=1168],lastUse=Mon Jan 05 15:58:29 UTC 1970,readBufferPosition=-1,socketTimeout=org.snmp4j.transport.DefaultTcpTransportMapping$SocketTimeout@77b7a02b]}
2025-05-24 16:27:16.753 Trap.0 DEBUG Waking up selector for new message
2025-05-24 16:27:16.753 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Adding operation 4 for: SocketEntry[peerAddress=127.0.0.1/42174,socket=Socket[addr=/127.0.0.1,port=42174,localport=1168],lastUse=Mon Jan 05 15:58:29 UTC 1970,readBufferPosition=-1,socketTimeout=org.snmp4j.transport.DefaultTcpTransportMapping$SocketTimeout@77b7a02b]
2025-05-24 16:27:16.754 Trap.0 INFO Message from 127.0.0.1/42174 not dispatched, reason: statusInfo=1.3.6.1.6.3.15.1.1.4.0 = 0, status=1410
2025-05-24 16:27:16.754 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is writable
2025-05-24 16:27:16.754 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Sent message with length 103 to 127.0.0.1/42174: 30:65:02:01:03:30:10:02:03:00:b0:6e:02:03:00:ff:ff:04:01:00:02:01:03:04:1d:30:1b:04:0d:80:00:13:70:01:7f:00:01:01:bd:df:0c:88:02:01:00:02:01:00:04:00:04:00:04:00:30:2f:04:0d:80:00:13:70:01:7f:00:01:01:bd:df:0c:88:04:00:a8:1c:02:01:00:02:01:00:02:01:00:30:11:30:0f:06:0a:2b:06:01:06:03:0f:01:01:04:00:41:01:00
2025-05-24 16:27:16.754 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is readable
2025-05-24 16:27:16.754 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is reading
2025-05-24 16:27:16.754 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Reading header 6 bytes from 0.0.0.0/1168
2025-05-24 16:27:16.754 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Message length is org.snmp4j.transport.MessageLength[headerLength=2,payloadLength=101]
2025-05-24 16:27:16.754 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Message completed with 103 bytes and 103 buffer limit
2025-05-24 16:27:16.754 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Received message from 0.0.0.0/1168 with length 103: 30:65:02:01:03:30:10:02:03:00:b0:6e:02:03:00:ff:ff:04:01:00:02:01:03:04:1d:30:1b:04:0d:80:00:13:70:01:7f:00:01:01:bd:df:0c:88:02:01:00:02:01:00:04:00:04:00:04:00:30:2f:04:0d:80:00:13:70:01:7f:00:01:01:bd:df:0c:88:04:00:a8:1c:02:01:00:02:01:00:02:01:00:30:11:30:0f:06:0a:2b:06:01:06:03:0f:01:01:04:00:41:01:00
2025-05-24 16:27:16.754 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is writable
2025-05-24 16:27:16.754 Trap.0 DEBUG SNMPv3 header decoded: msgId=45166, msgMaxSize=65535, msgFlags=00, secModel=3
2025-05-24 16:27:16.755 Trap.0 DEBUG Accepting zero length security name
2025-05-24 16:27:16.755 Trap.0 DEBUG No cache entry found for popEntry by msgID=45166
2025-05-24 16:27:16.755 Trap.0 DEBUG RFC3412 §7.2.10 - Received PDU (msgID=45166) is a response or internal class message, but cached information for the msgID could not be found
2025-05-24 16:27:16.755 Trap.0 INFO Message from 0.0.0.0/1168 not dispatched, reason: statusInfo=noError, status=-1409
2025-05-24 16:27:21.840 main DEBUG Removed pending request with handle: PduHandle[1796148982]
Listening for SNMP traps on port 1168 using TCP
2025-05-24 16:28:16.768 Timer-0 DEBUG Socket has not been used for 60013 milliseconds, closing it
2025-05-24 16:28:16.769 Timer-0 INFO Socket to 127.0.0.1/42174 closed due to timeout
2025-05-24 16:28:16.769 Timer-0 DEBUG Socket has not been used for 60014 milliseconds, closing it
2025-05-24 16:28:16.769 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is readable
2025-05-24 16:28:16.769 Timer-0 INFO Socket to 0.0.0.0/1168 closed due to timeout
2025-05-24 16:28:16.769 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is reading
2025-05-24 16:28:16.770 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Selection key cancelled, skipping it
2025-05-24 16:28:36.011 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is acceptable
2025-05-24 16:28:36.011 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Adding operation 1 for: SocketEntry[peerAddress=127.0.0.1/56188,socket=Socket[addr=/127.0.0.1,port=56188,localport=1168],lastUse=Mon Jan 05 15:59:48 UTC 1970,readBufferPosition=-1,socketTimeout=null]
2025-05-24 16:28:36.011 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Firing transport state event: org.snmp4j.transport.TransportStateEvent[source=org.snmp4j.transport.DefaultTcpTransportMapping@7bf6b6c1,peerAddress=127.0.0.1/56188,newState=1,cancelled=false,causingException=null]
2025-05-24 16:28:36.011 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is reading
2025-05-24 16:28:36.012 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Reading header 6 bytes from 127.0.0.1/56188
2025-05-24 16:28:36.012 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Message length is org.snmp4j.transport.MessageLength[headerLength=3,payloadLength=168]
2025-05-24 16:28:36.012 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Message completed with 171 bytes and 171 buffer limit
2025-05-24 16:28:36.013 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Received message from 127.0.0.1/56188 with length 171: 30:81:a8:02:01:03:30:12:02:04:6b:68:30:c1:02:04:7f:ff:ff:ff:04:01:03:02:01:03:04:3d:30:3b:04:0d:80:00:13:70:01:7f:00:01:01:bd:df:0c:88:02:01:01:02:04:02:67:37:8e:04:09:6e:6f:74:6c:73:75:73:65:72:04:0c:6c:8b:33:f8:b8:62:87:5d:7c:80:69:93:04:08:00:00:00:01:b7:c9:0f:88:04:50:d0:57:6d:2b:d8:58:8d:80:82:d6:b8:a4:71:80:9f:e3:89:78:b2:47:69:bd:7a:18:3f:e5:d4:42:a4:c6:c7:42:8d:66:73:ae:03:4a:1c:95:a8:23:03:14:83:30:33:f8:be:d6:24:ab:ff:3d:71:ac:ff:b7:35:d6:ee:b5:55:d8:50:67:8c:54:64:c1:ab:04:1c:a2:ea:da:f3:88:28:c9
2025-05-24 16:28:36.013 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is readable
2025-05-24 16:28:36.013 Trap.0 DEBUG SNMPv3 header decoded: msgId=1801990337, msgMaxSize=2147483647, msgFlags=03, secModel=3
2025-05-24 16:28:36.013 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Key is reading
2025-05-24 16:28:36.013 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Reading header -1 bytes from 127.0.0.1/56188
2025-05-24 16:28:36.013 Trap.0 DEBUG getUser(engineID=80:00:13:70:01:7f:00:01:01:bd:df:0c:88, securityName=notlsuser)
2025-05-24 16:28:36.013 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Socket closed remotely
2025-05-24 16:28:36.014 DefaultTCPTransportMapping_0.0.0.0/1168 DEBUG Firing transport state event: org.snmp4j.transport.TransportStateEvent[source=org.snmp4j.transport.DefaultTcpTransportMapping@7bf6b6c1,peerAddress=127.0.0.1/56188,newState=2,cancelled=false,causingException=null]
2025-05-24 16:28:36.031 Trap.0 DEBUG SHA-1First digest: 9a:6a:6e:75:a8:01:78:fc:37:db:eb:8c:92:8e:51:a2:cd:82:46:88
2025-05-24 16:28:36.031 Trap.0 DEBUG SHA-1localized key: 5c:8d:32:e3:1a:ad:d4:b0:41:69:4f:df:3b:17:f2:e3:6b:89:b5:64
2025-05-24 16:28:36.041 Trap.0 DEBUG SHA-1First digest: 8e:39:37:8a:e0:64:b9:5e:fc:7c:5f:e2:d9:cc:94:97:44:4c:97:eb
2025-05-24 16:28:36.041 Trap.0 DEBUG SHA-1localized key: 5b:5c:e0:fe:0f:6b:d9:d2:97:64:ce:ba:53:06:18:34:db:b8:81:32
2025-05-24 16:28:36.043 Trap.0 DEBUG Adding user notlsuser = UsmUser[secName=notlsuser,authProtocol=1.3.6.1.6.3.10.1.1.3,authPassphrase=5c:8d:32:e3:1a:ad:d4:b0:41:69:4f:df:3b:17:f2:e3:6b:89:b5:64,privProtocol=1.3.6.1.6.3.10.1.2.2,privPassphrase=5b:5c:e0:fe:0f:6b:d9:d2:97:64:ce:ba:53:06:18:34,localizationEngineID=80:00:13:70:01:7f:00:01:01:bd:df:0c:88]
2025-05-24 16:28:36.043 Trap.0 DEBUG CheckTime: received message outside time window (authoritative):engineBoots differ 0!=1
2025-05-24 16:28:36.043 Trap.0 DEBUG RFC3414 §3.2.7.a Not in time window; engineID=‘80:00:13:70:01:7f:00:01:01:bd:df:0c:88’, engineBoots=1, engineTime=40318862
2025-05-24 16:28:36.043 Trap.0 INFO Message from 127.0.0.1/56188 not dispatched, reason: statusInfo=1.3.6.1.6.3.15.1.1.2.0 = 0, status=1411
2025-05-24 16:29:36.196 Timer-0 DEBUG Socket has not been used for 60182 milliseconds, closing it
2025-05-24 16:29:36.197 Timer-0 INFO Socket to 127.0.0.1/56188 closed due to timeout
Command:
snmptrap -v 3 -e 0x80001370017f000101bddf0c88 -u notlsuser -a SHA -A authPass -x DES -X privPass -l authPriv -r 1 tcp:0.0.0.0:1168
40 “1.1.1.1”