Hello,
I’m trying to send a GET request to a device and I’m getting the following DEBUG output:
Initialized Salt to 18981ce190da4167.
UDP receive buffer size for socket 0.0.0.0/0 is set to: 65507
Adding user JGB = UsmUser[secName=JGB,authProtocol=1.3.6.1.6.3.10.1.1.2,authPassphrase=Whats_My_Name,privProtocol=1.3.6.1.4.1.4976.2.2.1.2.2,privPassphrase=Francis123,localizationEngineID=null]
RFC3414 §3.1.4.b Outgoing message is not encrypted
Adding cache entry: StateReference[msgID=49808,pduHandle=PduHandle[1841946943],securityEngineID=,securityModel=org.snmp4j.security.USM@5b37e0d2,securityName=JGB,securityLevel=1,contextEngineID=,contextName=,retryMsgIDs=null]
Running pending sync request with handle PduHandle[1841946943] and retry count left 0
Sending message to 192.168.0.23/161 with length 60: 30:3a:02:01:03:30:10:02:03:00:c2:90:02:03:00:ff:ff:04:01:04:02:01:03:04:10:30:0e:04:00:02:01:00:02:01:00:04:00:04:00:04:00:30:11:04:00:04:00:a0:0b:02:01:00:02:01:00:02:01:00:30:00
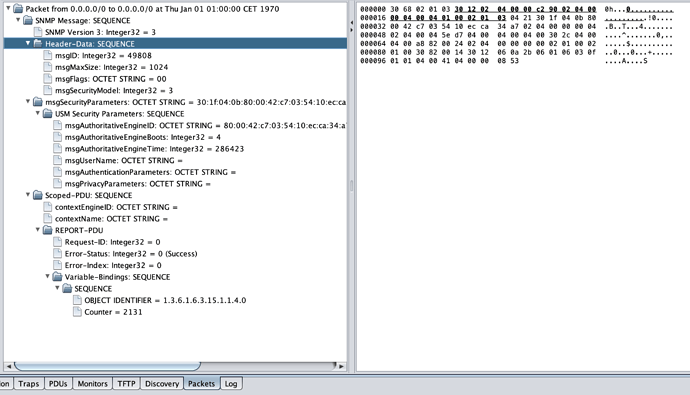
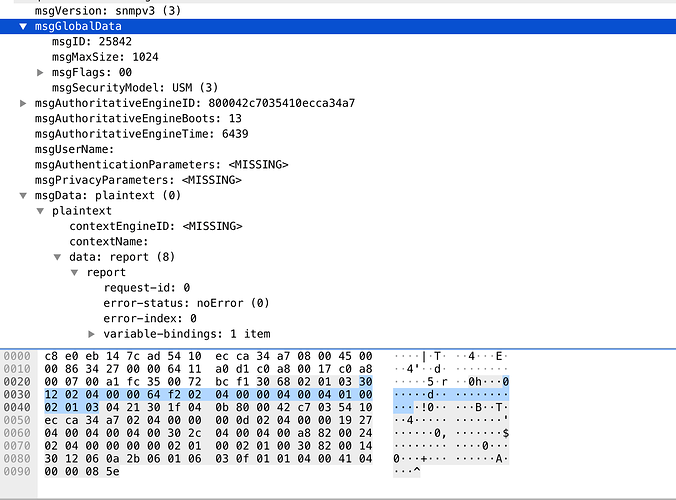
Received message from /192.168.0.23/161 with length 106: 30:68:02:01:03:30:12:02:04:00:00:c2:90:02:04:00:00:04:00:04:01:00:02:01:03:04:21:30:1f:04:0b:80:00:42:c7:03:54:10:ec:ca:34:a7:02:04:00:00:00:04:02:04:00:04:5e:d7:04:00:04:00:04:00:30:2c:04:00:04:00:a8:82:00:24:02:04:00:00:00:00:02:01:00:02:01:00:30:82:00:14:30:12:06:0a:2b:06:01:06:03:0f:01:01:04:00:41:04:00:00:08:53
SNMPv3 header decoded: msgId=49808, msgMaxSize=1024, msgFlags=00, secModel=3
MPv3 parse error: The actual length of the SEQUENCE object org.snmp4j.mp.MPv3$HeaderData is 15, but 18 was expected
java.io.IOException: The actual length of the SEQUENCE object org.snmp4j.mp.MPv3$HeaderData is 15, but 18 was expected
at org.snmp4j.asn1.BER.checkSequenceLength(BER.java:967)
at org.snmp4j.mp.MPv3$HeaderData.decodeBER(MPv3.java:739)
at org.snmp4j.mp.MPv3.prepareDataElements(MPv3.java:1137)
at org.snmp4j.MessageDispatcherImpl.dispatchMessage(MessageDispatcherImpl.java:278)
at org.snmp4j.MessageDispatcherImpl.processMessage(MessageDispatcherImpl.java:390)
at org.snmp4j.MessageDispatcherImpl.processMessage(MessageDispatcherImpl.java:350)
at org.snmp4j.transport.AbstractTransportMapping.fireProcessMessage(AbstractTransportMapping.java:76)
at org.snmp4j.transport.DefaultUdpTransportMapping$ListenThread.run(DefaultUdpTransportMapping.java:430)
at java.lang.Thread.run(Thread.java:748)
Message from 192.168.0.23/161 not dispatched, reason: statusInfo=noError, status=-1408
Request timed out: 1841946943
Removed pending request with handle: PduHandle[1841946943]
Removed cache entry: StateReference[msgID=49808,pduHandle=null,securityEngineID=,securityModel=org.snmp4j.security.USM@5b37e0d2,securityName=JGB,securityLevel=1,contextEngineID=,contextName=,retryMsgIDs=null]
ResponsePDU: null
Can you please advise on how to troubleshoot this issue?
Thanks.