Hi,
After enabled debugging -DCMAKE_BUILD_TYPE=Debug both SNMP++ 3.5.1 and Agent++ 4.6.1, somehow the debug log displays 20 bytes hex but backtrace shows engine_id=“\200” with correct engine_id_len=20. Seems like it was failed in MD5_PROCESS(&md5_hash_state, password_buf, 64);
We had debug log
password: MD5UserAuthPassword.
engineID: 80 00 13 70 05 64 65 76 73 69 6C 2D 6C 69 6E 2D 30 31 12 60
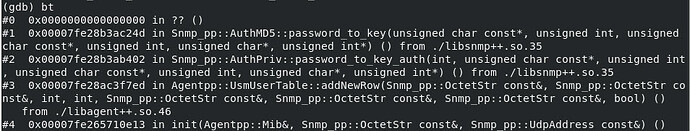
We had backtrace
#0 0x0000000000000000 in ?? ()
#1 0x00007fffee9d18ba in Snmp_pp::AuthMD5::password_to_key (this=0x7fff900020e0, password=0x7fff9002e550 “MD5UserAuthPassword”, password_len=19, engine_id=0x7fff90001390 “\200”, engine_id_len=20, key=0x7ffff7ee53e0 “”, key_len=0x7ffff7ee53dc) at auth_priv.cpp:1185
#2 0x00007fffee9d0932 in Snmp_pp::AuthPriv::password_to_key_auth (this=0x7fff90001f50, auth_prot=2, password=0x7fff9002e550 “MD5UserAuthPassword”, password_len=19, engine_id=0x7fff90001390 “\200”, engine_id_len=20, key=0x7ffff7ee53e0 “”, key_len=0x7ffff7ee53dc) at auth_priv.cpp:818
#3 0x00007fffee264cd9 in Agentpp::UsmUserTable::addNewRow (this=0x7fff9002ced0, userName=…, securityName=…, authProtocol=2, privProtocol=1, authPassword=…, privPassword=…, engineID=…, addPassWordsToUSM=false) at v3_mib.cpp:661
#4 0x00007fffcb2ca179 in init(Agentpp::Mib&, Snmp_pp::OctetStr const&, Snmp_pp::UdpAddress const&) ()
Note:
auth_priv.cpp:1185
MD5_PROCESS(&md5_hash_state, password_buf, 64);
auth_priv.cpp:818
int res = a->password_to_key(password, password_len,
engine_id, engine_id_len,
key, key_len);
v3_mib.cpp:661
int res = usm->get_auth_priv()->password_to_key_auth(
authProtocol,
authPassword.data(),
authPassword.len(),
engineID.data(), engineID.len(),
authKey, &authKeyLength);