Hi Frank,
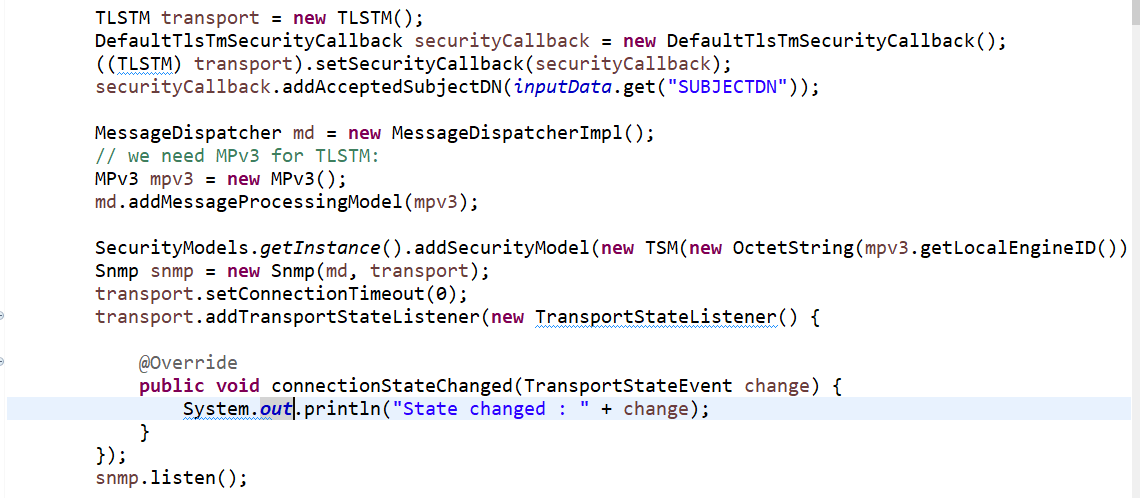
Even with latest jar I was facing “rejected because issuer and subject DN not accepted”, after debugging I noticed, in DefaultTlsTmSecurityCallback.isServerCertificateAccepted
String subject = peerCertificateChain[0].getSubjectDN().getName();
was not matching. The value was in hex for email and was failing
Eg: 3.6.3 non-working code, received subject= 1.2.840.113549.1.9.1=#160e6e696170406e6f6b69612e636f6d,CN=abc,OU=lmn,O=xyz, L=abc, ST=lmn, C=xyz
2.8.7 working code, received subject= EMAILADDRESS=niap@nokia.com, CN=abc, OU=lmn, O=xyz, L=abc, ST=lmn, C=xyz
Hence, I identified and used AcceptedIssuerDN and proceeded with tests instead of relying on AcceptedSubjectDN. Any information on above observation will be helpful for future.
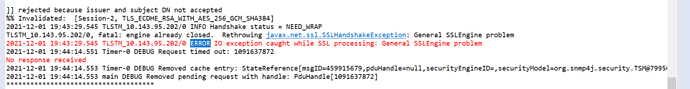
Actual issue test result:
I see the fix is working for the use case. Minor observation was state change fired and logged is STATE_CLOSED and not STATE_DISCONNECTED_REMOTELY.
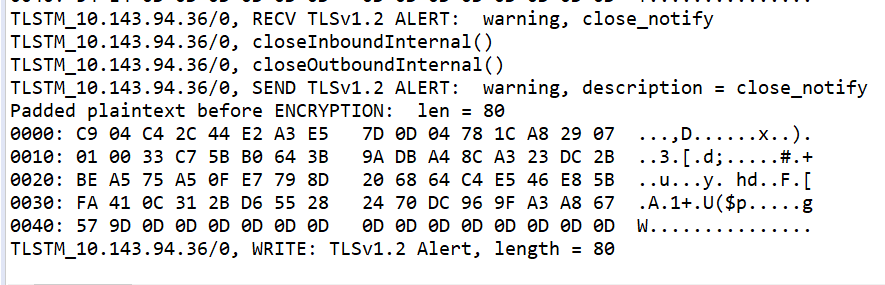
Logs for further info:
TLSTM_10.143.92.142/0, RECV TLSv1.2 ALERT: warning, close_notify
TLSTM_10.143.92.142/0, closeInboundInternal()
TLSTM_10.143.92.142/0, closeOutboundInternal()
2021-12-06 16:05:59.214 TLSTM_10.143.92.142/0 DEBUG Running delegated task on SocketEntry[peerAddress=135.249.189.239/10161,socket=Socket[addr=135.249.189.239/135.249.189.239,port=10161,localport=51536],lastUse=Sun Jan 11 01:30:46 IST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=31 lim=31 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outAppBuffer=null,outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null]: Status = CLOSED HandshakeStatus = NEED_WRAP
bytesConsumed = 31 bytesProduced = 0
TLSTM_10.143.92.142/0, called closeOutbound()
TLSTM_10.143.92.142/0, closeOutboundInternal()
2021-12-06 16:05:59.214 TLSTM_10.143.92.142/0 INFO TLS connection to 135.249.189.239/10161 is closed
2021-12-06 16:05:59.214 TLSTM_10.143.92.142/0 DEBUG Firing transport state event: org.snmp4j.transport.TransportStateEvent[source=org.snmp4j.transport.TLSTM@1dd02175,peerAddress=135.249.189.239/10161,newState=4,cancelled=false,causingException=null]
TCPDump:
Thanks for all the support 
Further more 
We are using java 8 and we were in need of fix in java 8 support snmp4j version which is latest 2.8.7 so far. Can you please check if the same can be supported in java 8.