When a client connects, I receive it’s org.snmp4j.transport.TransportStateEvent and store the peer address so I can send TLS/TCP based ‘broadcasts’ back to all connected clients. In the non TLS implementation, I simply stored a new instance of org.snmp4j.UserTarget
06 Nov 2019 16:05:15,943 [org.snmp4j.Snmp:] DEBUG - Fire process PDU event: CommandResponderEvent[securityModel=4, securityLevel=3, maxSizeResponsePDU=32743, pduHandle=PduHandle[470560328], stateReference=StateReference[msgID=6292881,pduHandle=null,securityEngineID=80:00:13:70:04:6d:61:6e:61:67:65:72:2d:44:4c:50:30:31:35:36:30,securityModel=org.snmp4j.security.TSM@7546dc9e,securityName=localhost,securityLevel=3,contextEngineID=80:00:13:70:04:6d:61:6e:61:67:65:72:2d:44:4c:50:30:31:35:36:30,contextName=,retryMsgIDs=null], pdu=SET[{contextEngineID=80:00:13:70:04:6d:61:6e:61:67:65:72:2d:44:4c:50:30:31:35:36:30, contextName=}, requestID=470560328, errorStatus=0, errorIndex=0, VBS[1.3.6.1.4.1.8419.20.1.2.8.0 = TRUE; 1.3.6.1.4.1.8419.20.1.2.10.0 = jdmarti1]], messageProcessingModel=3, securityName=localhost, processed=false, peerAddress=127.0.0.1/63616, transportMapping=mil.navy.e6b.block1.sysman.snmp.transport.ServerTLSTransportMapping@397347b3, tmStateReference=null]
06 Nov 2019 16:05:15,943 [mil.navy.e6b.block1.sysman.manager.handler.manager.SetCB:] INFO - reset Sysman initiated by jdmarti1
06 Nov 2019 16:05:15,944 [org.snmp4j.mp.MPv3:] DEBUG - Removed cache entry: StateReference[msgID=6292881,pduHandle=null,securityEngineID=80:00:13:70:04:6d:61:6e:61:67:65:72:2d:44:4c:50:30:31:35:36:30,securityModel=org.snmp4j.security.TSM@7546dc9e,securityName=localhost,securityLevel=3,contextEngineID=80:00:13:70:04:6d:61:6e:61:67:65:72:2d:44:4c:50:30:31:35:36:30,contextName=,retryMsgIDs=null]
06 Nov 2019 16:05:15,944 [org.snmp4j.transport.TLSTM:] DEBUG - Looking up connection for destination ‘127.0.0.1/63616’ returned: SocketEntry[peerAddress=127.0.0.1/63616,socket=Socket[addr=127.0.0.1/127.0.0.1,port=63616,localport=7835],lastUse=Mon Jan 19 12:12:41 CST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null]
06 Nov 2019 16:05:15,944 [org.snmp4j.transport.TLSTM:] DEBUG - {127.0.0.1/63810=SocketEntry[peerAddress=127.0.0.1/63810,socket=Socket[addr=127.0.0.1/127.0.0.1,port=63810,localport=7835],lastUse=Mon Jan 19 12:04:41 CST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null], 127.0.0.1/63619=SocketEntry[peerAddress=127.0.0.1/63619,socket=Socket[addr=127.0.0.1/127.0.0.1,port=63619,localport=7835],lastUse=Mon Jan 19 11:58:14 CST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null], 127.0.0.1/63616=SocketEntry[peerAddress=127.0.0.1/63616,socket=Socket[addr=127.0.0.1/127.0.0.1,port=63616,localport=7835],lastUse=Mon Jan 19 12:12:41 CST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null]}
06 Nov 2019 16:05:15,944 [org.snmp4j.transport.TLSTM:] DEBUG - Waking up selector for new message
06 Nov 2019 16:05:15,944 [org.snmp4j.transport.TLSTM:] DEBUG - Adding operation 4 for: SocketEntry[peerAddress=127.0.0.1/63616,socket=Socket[addr=127.0.0.1/127.0.0.1,port=63616,localport=7835],lastUse=Mon Jan 19 12:12:41 CST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null]
06 Nov 2019 16:05:15,944 [org.snmp4j.transport.TLSTM:] DEBUG - Key is writable
06 Nov 2019 16:05:15,944 [org.snmp4j.transport.TLSTM:] DEBUG - Sending message with length 116 to 127.0.0.1/63616: 30:72:02:01:03:30:10:02:03:60:05:91:02:03:00:80:00:04:01:03:02:01:04:04:00:30:59:04:15:80:00:13:70:04:6d:61:6e:61:67:65:72:2d:44:4c:50:30:31:35:36:30:04:00:a2:3e:02:04:1c:0c:2e:48:02:01:00:02:01:ff:30:30:30:14:06:0c:2b:06:01:04:01:c1:63:14:01:02:08:00:04:04:54:52:55:45:30:18:06:0c:2b:06:01:04:01:c1:63:14:01:02:0a:00:04:08:6a:64:6d:61:72:74:69:31
06 Nov 2019 16:05:15,945 [org.snmp4j.transport.TLSTM:] DEBUG - Writing TLS outNetBuffer(PAYLOAD): java.nio.HeapByteBuffer[pos=0 lim=197 cap=32768]
06 Nov 2019 16:05:15,945 [org.snmp4j.transport.TLSTM:] DEBUG - Wrote TLS 197 bytes from outNetBuffer(PAYLOAD)
06 Nov 2019 16:05:15,945 [org.snmp4j.transport.TLSTM:] DEBUG - Payload sent completely
06 Nov 2019 16:05:15,945 [org.snmp4j.transport.TLSTM:] DEBUG - Key is writable
06 Nov 2019 16:05:17,496 [org.snmp4j.mp.MPv3:] DEBUG - Adding cache entry: StateReference[msgID=6253355,pduHandle=PduHandle[660356043],securityEngineID=80:00:13:70:04:6d:61:6e:61:67:65:72:2d:44:4c:50:30:31:35:36:30,securityModel=org.snmp4j.security.TSM@7546dc9e,securityName=sysmanManagerTLSSN,securityLevel=3,contextEngineID=80:00:13:70:04:6d:61:6e:61:67:65:72:2d:44:4c:50:30:31:35:36:30,contextName=,retryMsgIDs=null]
java.io.IOException: Transport state reference does not match existing reference for this session/target
at org.snmp4j.transport.TLSTM$ServerThread.sendMessage(TLSTM.java:1230)
at org.snmp4j.transport.TLSTM.sendMessage(TLSTM.java:477)
at org.snmp4j.transport.TLSTM.sendMessage(TLSTM.java:69)
at org.snmp4j.MessageDispatcherImpl.sendMessage(MessageDispatcherImpl.java:203)
at org.snmp4j.MessageDispatcherImpl.sendPdu(MessageDispatcherImpl.java:522)
at org.snmp4j.Snmp.sendMessage(Snmp.java:1087)
at org.snmp4j.Snmp.send(Snmp.java:968)
at org.snmp4j.Snmp.send(Snmp.java:961)
at org.snmp4j.Snmp.send(Snmp.java:926)
at mil.navy.e6b.block1.sysman.snmp.SNMP.trap(SNMP.java:395)
at mil.navy.e6b.block1.sysman.snmp.SNMP.broadcast(SNMP.java:430)
at mil.navy.e6b.block1.sysman.manager.task.ClientUpdateTask.sendToStatusClients(ClientUpdateTask.java:85)
at mil.navy.e6b.block1.sysman.manager.task.ClientUpdateTask.run(ClientUpdateTask.java:464)
at java.util.concurrent.Executors$RunnableAdapter.call(Executors.java:511)
at java.util.concurrent.FutureTask.run(FutureTask.java:266)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624)
at java.lang.Thread.run(Thread.java:748)
06 Nov 2019 16:05:17,496 [org.snmp4j.transport.TLSTM:] DEBUG - Looking up connection for destination ‘127.0.0.1/63616’ returned: SocketEntry[peerAddress=127.0.0.1/63616,socket=Socket[addr=127.0.0.1/127.0.0.1,port=63616,localport=7835],lastUse=Mon Jan 19 12:12:41 CST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null]
06 Nov 2019 16:05:17,496 [org.snmp4j.transport.TLSTM:] DEBUG - {127.0.0.1/63810=SocketEntry[peerAddress=127.0.0.1/63810,socket=Socket[addr=127.0.0.1/127.0.0.1,port=63810,localport=7835],lastUse=Mon Jan 19 12:04:41 CST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null], 127.0.0.1/63619=SocketEntry[peerAddress=127.0.0.1/63619,socket=Socket[addr=127.0.0.1/127.0.0.1,port=63619,localport=7835],lastUse=Mon Jan 19 11:58:14 CST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null], 127.0.0.1/63616=SocketEntry[peerAddress=127.0.0.1/63616,socket=Socket[addr=127.0.0.1/127.0.0.1,port=63616,localport=7835],lastUse=Mon Jan 19 12:12:41 CST 1970,inNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],inAppBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],outNetBuffer=java.nio.HeapByteBuffer[pos=0 lim=32768 cap=32768],socketTimeout=null]}
06 Nov 2019 16:05:17,496 [org.snmp4j.transport.TLSTM:] ERROR - TransportStateReferences refNew=TransportStateReference[transport=mil.navy.e6b.block1.sysman.snmp.transport.ServerTLSTransportMapping@397347b3, address=127.0.0.1/63616, securityName=sysmanManagerTLSSN, requestedSecurityLevel=authPriv, transportSecurityLevel=undefined, sameSecurity=false, sessionID=null, certifiedIdentity=null],refOld=TransportStateReference[transport=mil.navy.e6b.block1.sysman.snmp.transport.ServerTLSTransportMapping@397347b3, address=127.0.0.1/63616, securityName=localhost, requestedSecurityLevel=authPriv, transportSecurityLevel=authPriv, sameSecurity=true, sessionID=1, certifiedIdentity=null] do not match, message dropped
06 Nov 2019 16:05:17,496 [mil.navy.e6b.block1.sysman.snmp.SNMPv3:] FATAL - Exception sending trap - org.snmp4j.MessageException: Transport state reference does not match existing reference for this session/target
How do I create or retrieve a proper “callback” target for a connected client from a received org.snmp4j.transport.TransportStateEvent?
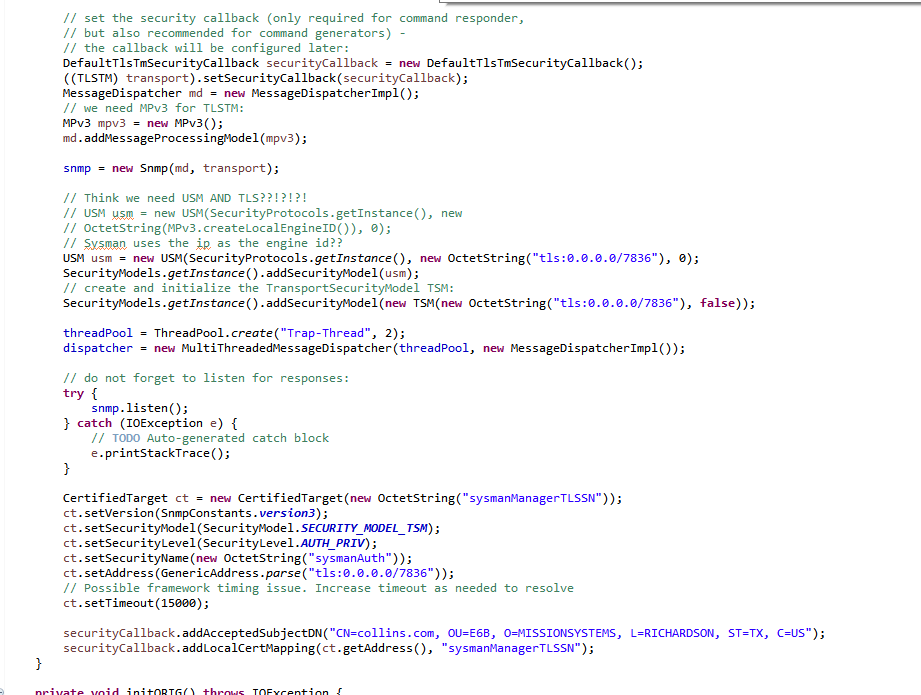
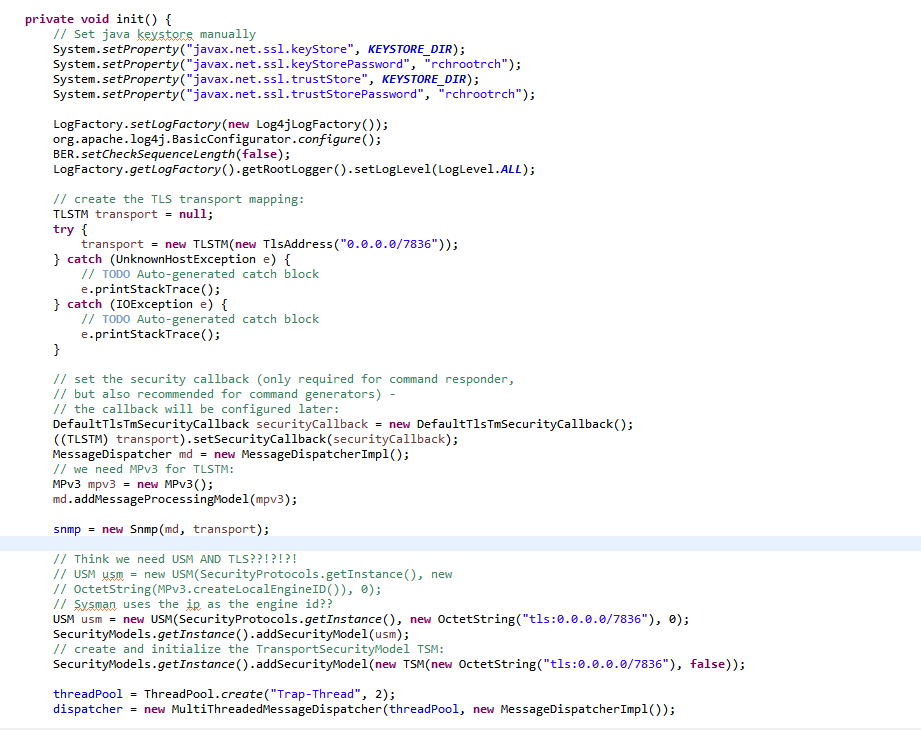
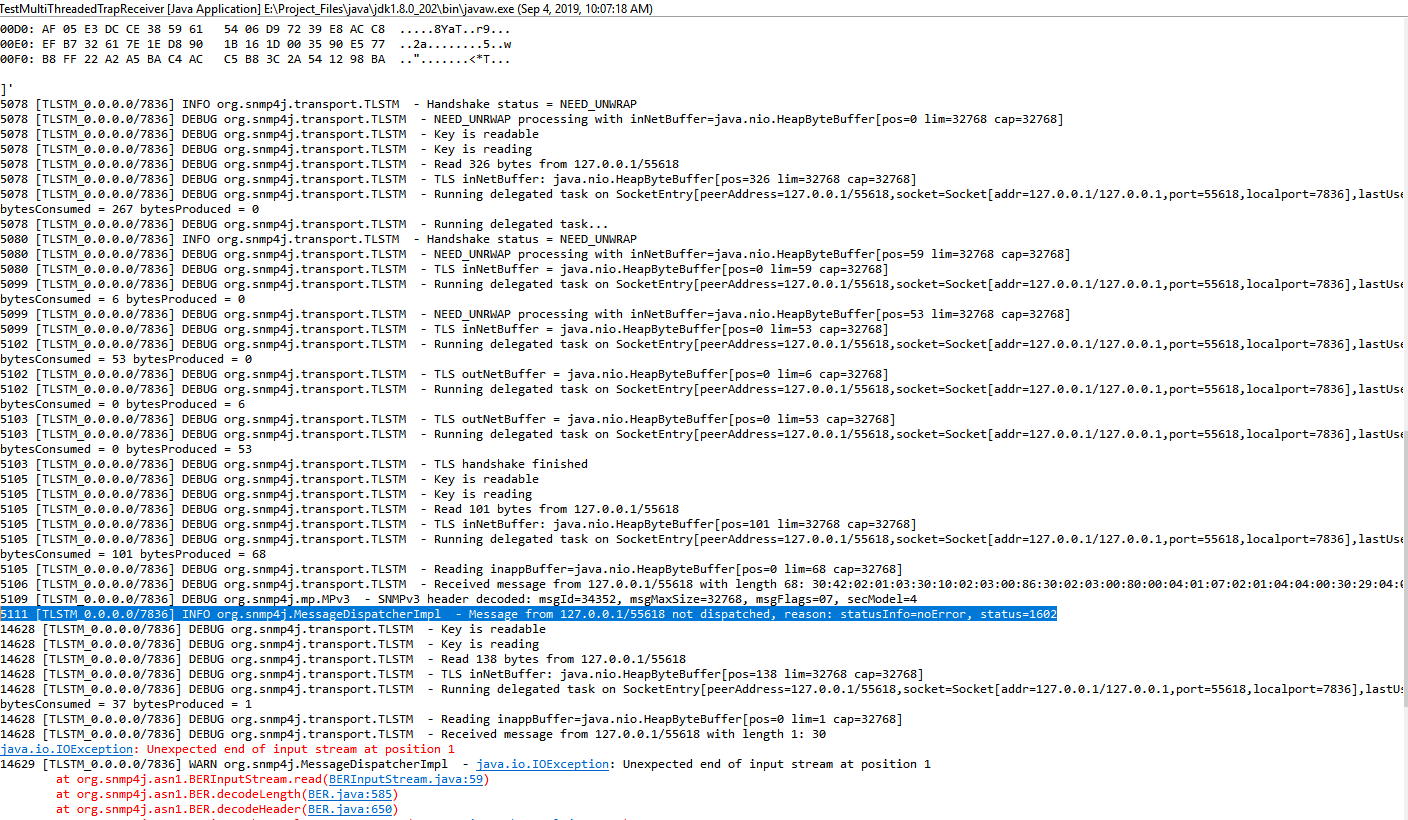
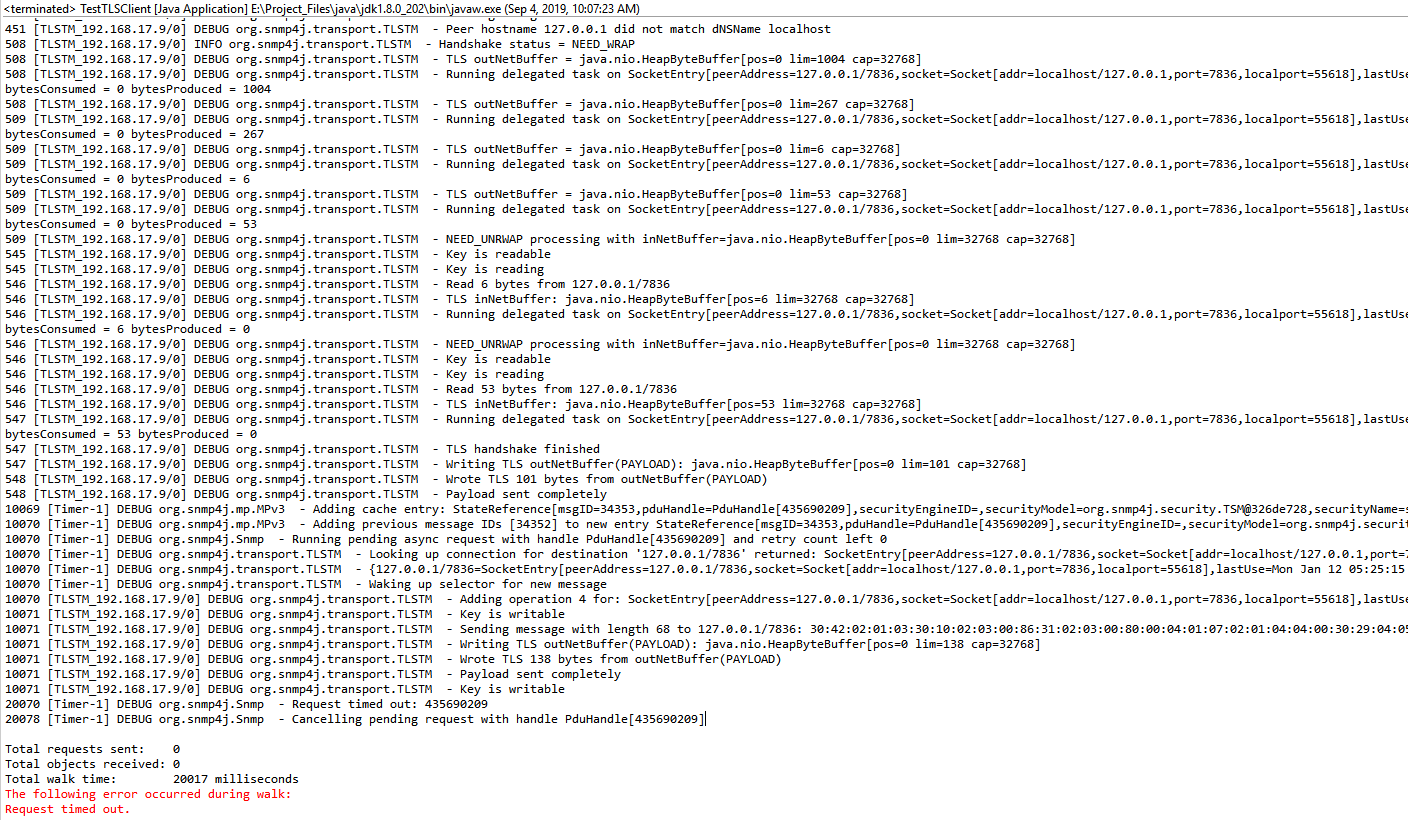
 - You found dead code! The CommandResponderEvent.getTmStateReference() will always return null. (This will be fixed in the next release and will basically implement the workaround below in that getter method)
- You found dead code! The CommandResponderEvent.getTmStateReference() will always return null. (This will be fixed in the next release and will basically implement the workaround below in that getter method)